- PRODUCTS
- Security Platform
- BioStar X | On-Prem SecurityNEW
- BioStar Air | Cloud Security
- BioStar 2
- Access Control
- Access Control Unit
- Biometric Readers
- RFID Readers
- Mobile Credential
- Peripherals
- Wireless Door Locks
- SOLUTIONS
- SUPPORT
- ABOUT
- device_hubHUB
- Blogs & Articles

Cloud vs. on-prem? Learn the real differences between access control models, and why the shift to the cloud may be your next best move.
After last week’s article, this is the second article in our cloud access control series, adapted from our latest eBook. If you want to dive deeper into the future of access technology, credential flexibility, and platform comparisons—download our full guide.
It’s a fair question. On-premise access control has been the industry standard for decades. It offers total infrastructure control, offline reliability, and deep customization.
So why change? The truth is, on-prem systems still do some things very well. But as organizations become more distributed and user expectations shift, those same systems start to show their age. What used to be strengths, like full local control, can turn into operational roadblocks.
Two approaches. One future.
In access control, the conversation often turns into a binary: cloud vs. on-premise. But it’s not that simple. Both approaches offer clear advantages, and specific limitations. The key is knowing which model fits your needs today, and which will still serve you tomorrow.
Let’s break it down.
On-premise access control: Integrated security for complex environments.
For years, on-premise access control systems have been the standard, especially in enterprise, industrial, and high-security environments. Everything is hosted locally: the server, the database, the credentials, and the door controllers. That tight coupling enables a level of control and system depth that cloud platforms are still catching up to.
On-premise solutions often support a broader range of features, integrating access control, alarm management, video surveillance, time and attendance, and visitor tracking into a single, unified system. They also offer direct, hardware-level integrations with third-party systems like fire panels or building automation, making them highly adaptable to complex security ecosystems. That architecture offers some real strengths:
ㆍTotal control over data, network, and infrastructure.
ㆍNo dependency on internet connectivity or cloud uptime.
ㆍLow-latency communication between components.
ㆍRobust local failover and redundancy options.
ㆍHigh compatibility with third-party hardware and building systems through direct wiring.
But it also comes with significant tradeoffs
ㆍRequires dedicated IT and physical infrastructure.
ㆍScaling across sites increases complexity and cost.
ㆍDifficult to manage remotely or adapt quickly.
ㆍManual software updates and hardware maintenance add overhead.
ㆍLess compatible with modern cloud tools or API-based workflows.
In an age of remote work, flexible access, and mobile-first management, on-prem systems, while still powerful, can become operational bottlenecks.
Cloud access control: Agility without the infrastructure.
Cloud-based access control takes a different approach. Instead of local servers, configurations, credentials, and data live in the cloud, accessible from anywhere, managed centrally through a web interface or mobile app.
The advantages are immediate:
ㆍNo on-site servers and limited infrastructure required.
ㆍManage all locations from a single dashboard.
ㆍRemote enrollment, access changes, and real-time monitoring, from anywhere.
ㆍFast deployment: ideal for growing or distributed operations.
ㆍContinuous software updates and built-in security patches.
ㆍEasier integration with other cloud-based solutions.
These benefits make cloud access control especially appealing for organizations looking to reduce IT overhead, improve operational agility, and support flexible work models.
But cloud also comes with tradeoffs to consider:
ㆍInternet dependency: Access control relies on a stable network connection. Local fallback, call it an offline mode, is essential in case of outages.
ㆍLess hardware customization: Some cloud platforms standardize hardware interactions, limiting deep customization.
ㆍRecurring subscription costs: OPEX-friendly , but long-term subscription models may exceed one-time CAPEX options.
ㆍVendor lock-in: With platform-centric ecosystems, switching providers can be complex once deployed at scale.
ㆍData residency & compliance: Depending on your region, storing access logs and biometric data in the cloud may require additional due diligence.
Cloud is not a silver bullet, but when built well, it can streamline operations, simplify deployments, and scale effortlessly across locations.
Quick comparison: Cloud vs. on-premise access control.
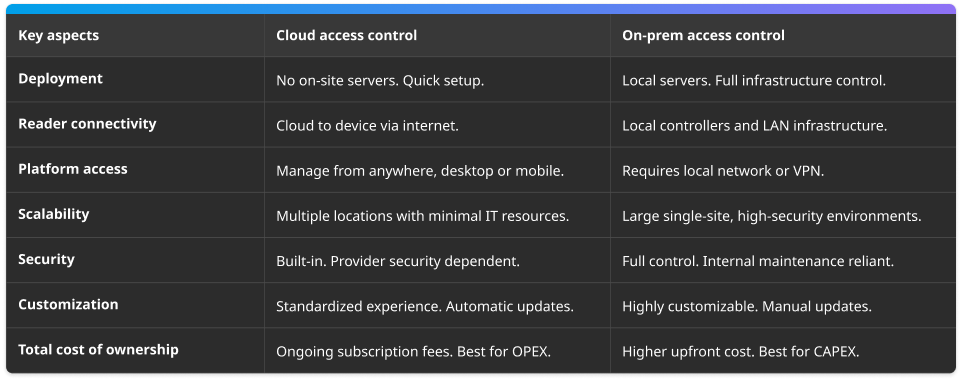
Cloud or on-premise? It’s not a binary choice, it’s about finding the right fit for your business model, growth strategy, and operational needs. On-prem systems still shine in tightly controlled, single-site environments. But if you’re managing distributed teams, growing locations, or prioritizing agility and low overhead, cloud platforms offer an undeniable edge.
In our next article, we’ll break down the different types of cloud access control systems, and explain why not all “cloud” solutions are created equal. Stay tuned.
Want the full story right now? Download the complete BioStar Air eBook for expert insights, real-world use cases, and side-by-side platform comparisons.











